Internet Safety Fundamentals Explained
Wiki Article
Things about Vpn Services
Table of ContentsThe Buzz on Cybersecurity TrainingThe Greatest Guide To Vpn ServicesGet This Report about Vpn ServicesParental Control Software Can Be Fun For AnyoneThe Greatest Guide To Internet SafetyAn Unbiased View of Vpn Services
If we speak about it particularly it's Part 2 of Avoidance of Electronic Crimes Act, 2016, that provides details regarding criminal activities of computer system misuse and to bill for the details criminal activity. Taking and abuse of individual data. As computer has many means via which individuals can take information and also abuse it, as computer is a device which is fast and also procedure any job swiftly, so when it pertains to the moving or copying information it does with convenience as well as in seconds.
If some prohibited or uncertified gain access to that has been utilized for hacking purpose, where an uncertified individual uses a computer system, network or the Web to hack the victim's system without having any type of kind of consent to get access and also control the system. Whenever the system is hacked the target don't understand anything that his/her information has been hacked and also most of the moment hackers do hacking to hazard the victim.
So, that the computer system or any kind of system will not be hacked easily as their safety of accessing system will certainly be high. When a crime is done by a private then he or she is obliged for specific crime then that person is billed with high quantity of money as the fees for underhanded abuse of somebody privacy, and also in some situations, there are imprisonment if the crook was associated with multiple crimes.
The Facts About Online Identity Protection Revealed
So, the grown-up youngster can easily access. These profane products have high threat damages the future of young generation, but the law states it is a crime to create as well as disperse off-color material that is bad for the young people that are listed below age of 18. Essentially, the act of significant crimes will be made use of to offer the punishment to the individual who uses computer modern technology as well as the Internet to acquire, spread or share/distribute the repulsive material which contain repulsive video clips, images.These companies have actually given center to report them on-line and also via their details call to make sure that the customer can report concerning the youngster sex-related misuse educate of images or videos in an extremely protective method so the criminal can be arrested and from the Net to get rid of and also wipe these sorts of obscene points or product.

How Internet Safety can Save You Time, Stress, and Money.
That triggers huge money loss to the person. All of us recognize that social websites and also applications are the resources through which people link as well as share their personal life events visit their website with good friends, but due to these instances related to on-line harassment is increasing everyday, where an individual utilizes Web services to maintain an eye on the target while remaining confidential as well as making use of public groups or web sites to obtain detail about their victim.
But that reason not only loss of money, but the clients' trust. To prevent from these kind of strikes banks must take protection preventative measures as well as safe procedure for the online purchases, to remain safe in future from this kind of accident. There are lots of legislations which gives protection to every customer of the Net from offenders who uses network to hurt the users, but the government needs to take some steps to make entities that instruct the companies who implement the law, that how to questions those crimes which is related to the Web as well as sell efficient method.
Getting The Online Identity Protection To Work
It is essential for each Internet customer to take the importance about the safety and security and laws basically which deals with the criminal activities that are brought on by the incorrect usage of computer. And also there ought to be a correct way for the protection administration to protect and shield the systems, as well as the respective information inside them.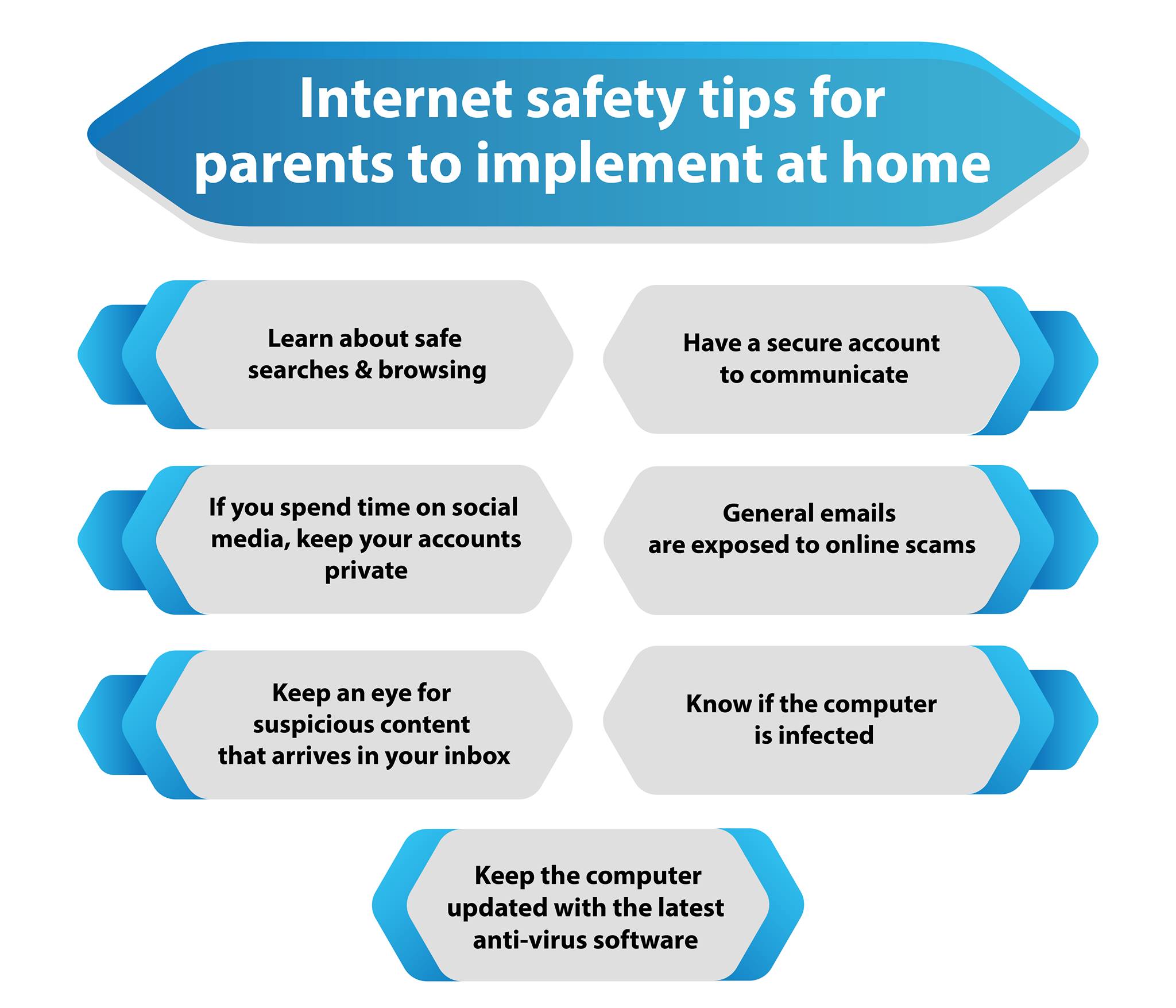
The value of cybersecurity in the digital globe is enormous. As our reliance on modern technology grows, so does our susceptability to these strikes. Cybersecurity helps to shield our information and systems from these hazards.
Vpn Services Things To Know Before You Get This
Cyber safety and security is necessary for students due to the fact that they commonly target online assaults. In a current situation, a group of students from a college in the United States was targeted by hackers that got to their individual info, including their Social Safety and security numbers as well as charge card info. The cyberpunks after that used this details to fraudulently bill hundreds of dollars to the students' credit rating cards.This situation highlights the relevance of cyber protection for pupils, who are usually the targets of cybercrime. If a trainee's anonymous personal info is taken in a cyber strike, maybe used to commit identity burglary. It might spoil the pupil's credit why not try here history, making it challenging for the trainee to obtain financings for college or an auto.
The significance of Cyber Safety for companies and companies can be seen when it comes to the target information breach. In this situation, cyberpunks were able to get accessibility to the target's consumer information, consisting of credit score as well as debit card details. It resulted in target needing to pay out millions of dollars in problems and also losing customer trust.
Getting My Online Identity Protection To Work
Another information breach example would be the Wan na, Cry ransomware strike, which targeted businesses as well as organizations worldwide. This attack led to the loss of information as well as cash for many companies, as well as some were even forced to close down (Cybersecurity training). accredited Moral Hacking programs for people to function in the direction of shielding information from breaches and also malware.If this information had actually fallen under the incorrect hands, it can have been utilized for identity burglary, fraud, or various other harmful purposes. In current years, there have actually been several top-level cyberattacks that have had a destructive effect on services and individuals. Parental control software. These are burglary of social safety and security numbers, checking account information, charge card details, as well as delicate information leaks
Report this wiki page